jkxx
*hv
- MBTI
- INFJ
- Enneagram
- 1w2
[tagging @Ginny and @Lady Jolanda]
This is a continuation of the thread about Microsoft snooping on users, except with some new and even more disturbing additions. (mods - feel free to place somewhere else, not sure what this would fall under but news for sure)
A brief recap - Ars Technica published a comprehensive article about Microsoft forcefully enabling telemetry transmission (spying on users) in Windows 10 even when the users wanted to opt out. Not only is the option turned on by default and disguised such that the user won't see it (*Microsoft has been forced to place a dialog up-front in more recent builds of Windows) but it cannot be entirely turned off either except in the enterprise version of Windows 10. Worse yet, utcsvc was back-ported to Windows 7 and 8 so those of you running these OSes are also running MS' "telemetry" spying malware.
To this end I did some digging and found out the spyware is implemented as a system service which cannot easily be stopped using the SCM (service control manager) and which relies on a "system" file owned by Trusted Installer and untouchable by the user even when logged in as admin. Worse yet, running a sfc /scannow or installing any major updates prompts Windows to re-scan the system32 folder and reinstall the spyware if it has been disabled somehow.
A temporary solution is my telemetry monitor tool* which uses some underhanded techniques to get access to the file and install a blank (but functional as a service DLL) alternative. Though it still needs much work such as adding it to startup so it can tell the user when Windows has managed to sneak the malware back into the OS.
So thinking this has solved the problem I became somewhat complacent about it figuring the data transmission has stopped with the disabling of utcsvc - unfortunately this assumption has turned out to be wrong.

A recent test session with Fiddler for an unrelated project showed Microsoft is now using the Windows Error Reporting component to send encrypted data to MS servers - thus a legitimate component of Windows once again zombified into a data mining/transmission component. In the screenshot the request fails since I've blocked the server with an external firewall (it cannot be blocked with the Windows firewall, Microsoft has added hard-coded exceptions so the network requests always succeed...), however it would have succeeded otherwise. Thus Microsoft appears to be adding a second route for data transmission through what have up to now been legitimate Windows components and services.
Most ironic bit however - MS has noticed Telemetry Monitor and now Windows Defenders flags it as malware which could be "dangerous to your computer." Bahahaaa..
* If there are any devs here and one of you is interested in picking up this code and developing it further please let me know. I'd like it to be easy to use and available to people, at least anyone interested in their privacy.
This is a continuation of the thread about Microsoft snooping on users, except with some new and even more disturbing additions. (mods - feel free to place somewhere else, not sure what this would fall under but news for sure)
A brief recap - Ars Technica published a comprehensive article about Microsoft forcefully enabling telemetry transmission (spying on users) in Windows 10 even when the users wanted to opt out. Not only is the option turned on by default and disguised such that the user won't see it (*Microsoft has been forced to place a dialog up-front in more recent builds of Windows) but it cannot be entirely turned off either except in the enterprise version of Windows 10. Worse yet, utcsvc was back-ported to Windows 7 and 8 so those of you running these OSes are also running MS' "telemetry" spying malware.
To this end I did some digging and found out the spyware is implemented as a system service which cannot easily be stopped using the SCM (service control manager) and which relies on a "system" file owned by Trusted Installer and untouchable by the user even when logged in as admin. Worse yet, running a sfc /scannow or installing any major updates prompts Windows to re-scan the system32 folder and reinstall the spyware if it has been disabled somehow.
A temporary solution is my telemetry monitor tool* which uses some underhanded techniques to get access to the file and install a blank (but functional as a service DLL) alternative. Though it still needs much work such as adding it to startup so it can tell the user when Windows has managed to sneak the malware back into the OS.
So thinking this has solved the problem I became somewhat complacent about it figuring the data transmission has stopped with the disabling of utcsvc - unfortunately this assumption has turned out to be wrong.
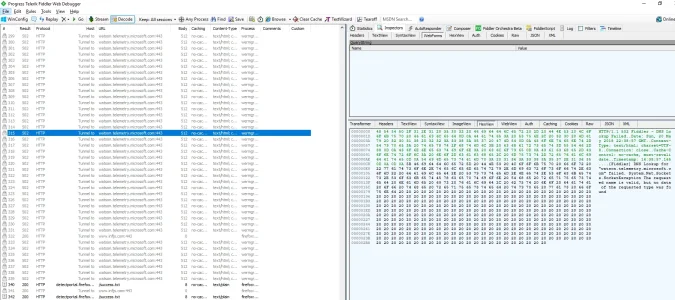
A recent test session with Fiddler for an unrelated project showed Microsoft is now using the Windows Error Reporting component to send encrypted data to MS servers - thus a legitimate component of Windows once again zombified into a data mining/transmission component. In the screenshot the request fails since I've blocked the server with an external firewall (it cannot be blocked with the Windows firewall, Microsoft has added hard-coded exceptions so the network requests always succeed...), however it would have succeeded otherwise. Thus Microsoft appears to be adding a second route for data transmission through what have up to now been legitimate Windows components and services.
Most ironic bit however - MS has noticed Telemetry Monitor and now Windows Defenders flags it as malware which could be "dangerous to your computer." Bahahaaa..
* If there are any devs here and one of you is interested in picking up this code and developing it further please let me know. I'd like it to be easy to use and available to people, at least anyone interested in their privacy.
